Quick take:
Popular NFT trader and crypto scam investigator ZachXBT has uncovered one of the groups behind NFT Discord hacks. According to ZachXBT, Cameron Redman is the alleged person behind the recent NFT Twitter hacks.
The NFT trader points to an incident in 2020 when the alleged hacker SIM swapped $37 million worth of bitcoin and bitcoin cash from a single person.
According to the NFT security researcher, since December 2021, more than 600 NFT Discord servers have been compromised, while at least 12 Twitter accounts related to NFTs have been hacked.
1/ Since Dec 2021 we’ve seen 600+ Discord servers compromised & 12+ NFT related Twitter accounts hacked as well. This has resulted in millions of dollars being stolen.
Welcome to part 2 of tracking down the people responsible. https://t.co/F5uoQsCwCc
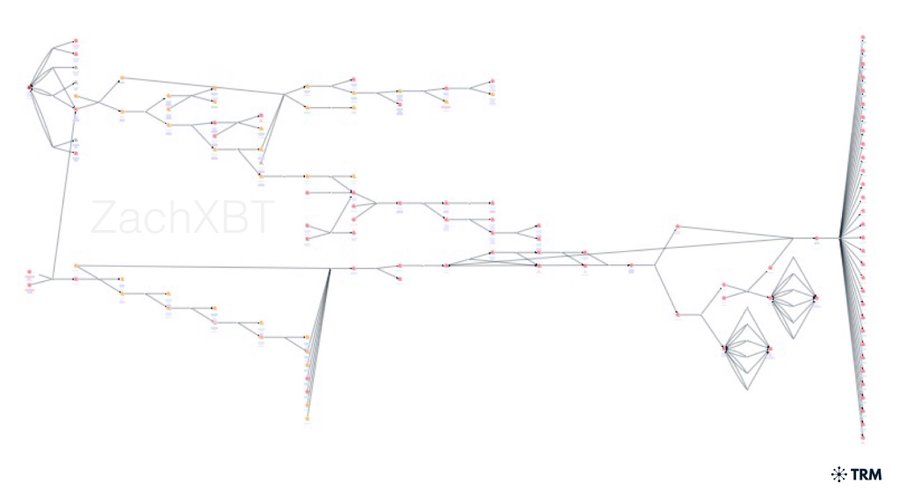
The Twitter user linked Redman to the 1,547 BTC and 60k BCH SIM swapped from crypto trader Josh Jones on February 22, 2020.
The hacker reportedly laundered the 60k BCH through hundreds of transactions in small amounts sent to centralised exchanges, according to the third post in the Twitter Thread.
A majority of the 1,547 BTC was sent to a chip mixer and crypto mixer platforms, with a small portion sent to small centralised exchanges.
Cameron Redman (underage at the time) was arrested and formally charged by Canadian police on November 17, 2021, recovering $5.4 million in crypto.
Fast-forward to May 2022, several NFT Twitter accounts with 2FA protection were hacked leading to millions worth of crypto stolen.
The list includes some of the most popular accounts on the platform leaving people confused as to how hackers managed to surpass a 2FA security.
6/ Since May 2022 we’ve seen popular NFT Twitter accounts hacked such as @beeple @jenkinsthevalet @nounsdao @deekaymotion @Zeneca_33 @frankdegods @KeyboardMonkey3 @franklinisbored & more
The majority of these accounts all had 2FA on leaving people confused how this might happen. pic.twitter.com/fd9hMbN6UU
The hacker was identified to be a person or group going by the name antihero after they were tracked to a forum marketplace SWAPD, where they wrote an advert for a panel on Twitter.
Antihero emerged with the name Cam on July 29, sparking curiosity as to whether it was the same Cameron Redman charged for a crypto scam in November 2020.
Redman later posted on Instagram a picture of himself outside a shopping centre. Further investigations revealed that the shopping centre was located in Canada, closer to the police station where Redman was arrested two years ago.
Towards the end of June, Redman had received 230 ETH plus 20 ETH in the address: 0x0214ee97e9d828e1e6aa49a85b89982a7dceacc7
The 20 ETH was a payment for lifetime access to the Twitter panel. ZachXBT was able to link the scammer’s address to the Nansen discord attack, and other Discord attacks.
15/ Just a few hours after the payment @nounsdao Twitter was hacked.
The scammers address had direct exposure to the JRNY club Twitter hacker, Nansen discord attack, and other Discord attacks.
Source:https://t.co/sTL2crJ1WP pic.twitter.com/bcT1qk1tJv
Redman had sold his Twitter panel access to renowned scammers HZ/Chase and Popbob, who did not shy away from showing off panel access to a security researcher who goes by the pseudonym Serpent.
Stay up to date:
Web3 VC and Market Maker Digital Wave Finance Launches DWF Labs
The University of Houston Is Eyeing the Industrial Metaverse in Collaboration with Nvidia
Ethereum Nets $4.7M Revenue from ENS Domains in August
Polygon Launches eDAO Platform to Bring Web2 Brands to Web3
NFT Blockchain Flow Announces $725M Ecosystem Fund to Accelerate Growth Across Its Ecosystem
MoonPay Raises $87M from 60 Celebrity Investors