Blockchain & Cryptocurrency , Cryptocurrency Fraud , Cybercrime
Criminals are doubling down on their use of information-stealing malware to target cryptocurrency being stored in internet-connected hot wallets.
See Also: Live Webinar | Remote Employees & the Great Resignation: How Are You Managing Insider Threats?
Call it “cryware,” say researchers at Microsoft, who have published a new report on the trend, which further highlights just how much criminals love cryptocurrency. Indeed, in 2021, they stole about $3.2 billion worth of cryptocurrency, which was a 516% increase compared to 2020, reports blockchain analytics firm Chainalysis.
Conceptually, targeting files that digitally store details pertaining to cryptocurrency is an obvious play for criminals. Hot wallets are internet-connected pieces of software – sometimes stand-alone applications or, in some cases, browser extensions called web wallets – that store the cryptographic details needed to access any cryptocurrency being storing therein. By stealing that data, crooks can instantly transfer the funds to a wallet they control (see: Cryptocurrency Wallets Targeted by Alien Malware Variant).
Thanks to the magic of cryptocurrency, the victim has no ability to claw the funds back, beyond filing a police report and hoping for the best.
Victims who opt to store such information elsewhere on their PC – for example, in a text file – are also at risk. The Microsoft researchers say in their report that attackers will typically search an entire PC for such information, regardless of where it’s being stored.
“To find hot wallet data such as private keys, seed phrases, and wallet addresses, attackers could use regular expressions – regexes – given how these typically follow a pattern of words or characters,” they write. “These patterns are then implemented in cryware, thus automating the process.”
To further increase the chance of success, some cryware also analyzes system memory for cryptocurrency data that’s being handled in unencrypted form – for example, if a hot wallet is displaying private keys in plaintext when a user is conducting a transaction. “This critical information might remain in the memory of a browser process performing these actions, thus compromising the wallet’s integrity,” the researchers say. “Such a scenario also allows an attacker to dump the browser process and obtain the private key.”
Keyloggers provide criminals with another tactic for stealing private keys to cryptocurrency wallets. “Even users who store their private keys on pieces of paper are vulnerable to keyloggers,” the Microsoft researchers say. “Copying and pasting sensitive data also don’t solve this problem, as some keyloggers also include screen-capturing capabilities.”
Indeed, another common tactic is watching cut-and-paste operations, to steal anything that looks as if it might be tied to cryptocurrency. But some attacks are even more pernicious. For example, some “clipping” malware watches to see if a cryptocurrency address gets copied to the clipboard. “Clippers typically use this functionality to detect when a user has copied a cryptocurrency address to which they intend to send funds – the clipper malware effectively hijacks the transaction by then substituting an address controlled by the hacker for the one copied by the user, thereby tricking the user into sending cryptocurrency to the hacker,” Chainalysis reports in its 2022 Crypto Crime Report.
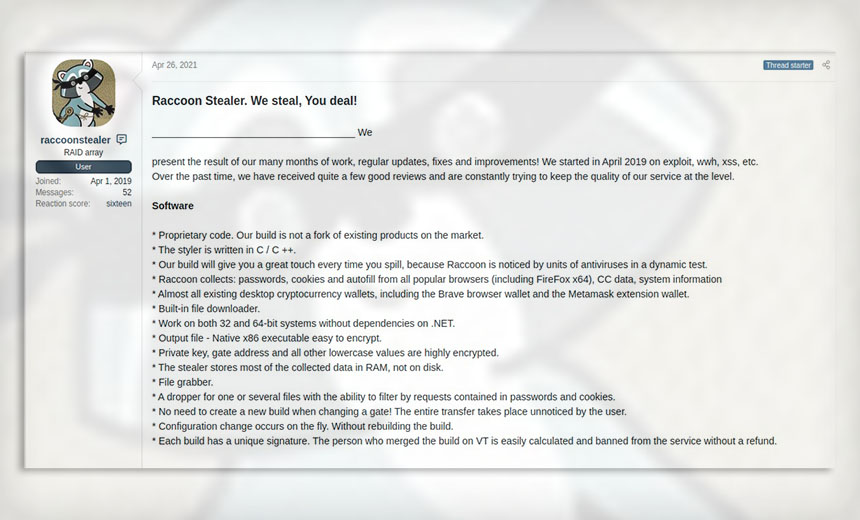
Information-stealing malware is widely available, including strains such as Cryptobot, RedLine, Mars and QuilClipper.
Some users of information-stealing malware pay a flat fee to license it and can do whatever they like.
“Infostealers are an inexpensive entry ramp into criminal activity,” security firm Sophos reports. “An entry-level, seven-day subscription to Raccoon Stealer, for example, only costs $75,” and includes a built-in clipper.
Some infostealers get procured as a service, which can come with terms and conditions that give the malware-as-a-service provider the right of first refusal on any data that gets stolen. In some cases, the agreement stipulates that the malware-as-a-service provider alone receives any and all stolen information that pertains to anything involving cryptocurrency.
Various infostealers also get regularly cracked and posted online.
According to chatter tracked by threat intelligence firm Kela, users of a cybercrime forum earlier this month reported that Mars Stealer appeared to no longer be getting updates. “Go buy redline stealer, it’s your best options,” a forum user responded. “If you want PM me for his telegram for buying.”
The interruption in Mars Stealer updates might be tied to a cracked version of Mars Stealer version 8 – including a “builder” for generating new strains of the malware plus a “panel” for managing infections – getting distributed for free to multiple cybercrime forums, according to discussions tracked by Kela.
Of course, information-stealing malware is but one tool in criminals’ cryptocurrency-stealing arsenal. Other approaches and targets include:
What can cryptocurrency users do to protect themselves?
Aside from the risk posed by volatility in the value of cryptocurrency, another is that even a single security misstep can leave users out of pocket. The ease with which cryptocurrency can be targeted and the massive potential payoff from a successful attack continue to draw new criminals into the fray. This is one reason why incident response experts recommend that organizations never stockpile cryptocurrency in the event they suffer a ransomware infection.
For anyone who does use or hold cryptocurrency, employing antivirus software to scan for information-stealing malware, locking hot wallets when not in use – to prevent them from being surreptitiously emptied – and practicing excellent password-handling hygiene remain essential, the Microsoft researchers say.
Likewise, experts recommend whenever possible using cold wallets, which store information offline, meaning information-stealing malware can’t touch it. The Microsoft researchers also recommend storing private keys using nondigital means, such as writing them down on paper and storing them somewhere safe. But as detailed above, even this approach isn’t foolproof, once it comes time to enter this information into a web browser or smartphone app.
Executive Editor, DataBreachToday & Europe, ISMG
Schwartz is an award-winning journalist with two decades of experience in magazines, newspapers and electronic media. He has covered the information security and privacy sector throughout his career. Before joining Information Security Media Group in 2014, where he now serves as the executive editor, DataBreachToday and for European news coverage, Schwartz was the information security beat reporter for InformationWeek and a frequent contributor to DarkReading, among other publications. He lives in Scotland.
Covering topics in risk management, compliance, fraud, and information security.
By submitting this form you agree to our Privacy & GDPR Statement
Cybercrime
Access Management
Blockchain & Cryptocurrency
Critical Infrastructure Security
Cryptocurrency Fraud
Continue »
90 minutes · Premium OnDemand
Overview
From heightened risks to increased regulations, senior leaders at all levels are pressured to improve their organizations’ risk management capabilities. But no one is showing them how – until now.
Learn the fundamentals of developing a risk management program from the man who wrote the book on the topic: Ron Ross, computer scientist for the National Institute of Standards and Technology. In an exclusive presentation, Ross, lead author of NIST Special Publication 800-37 – the bible of risk assessment and management – will share his unique insights on how to:
Sr. Computer Scientist & Information Security Researcher, National Institute of Standards and Technology (NIST)
Was added to your briefcase
Cryptocurrency-Stealing 'Cryware' Malware Attacks Surge
Cryptocurrency-Stealing 'Cryware' Malware Attacks Surge
Sign in now
Need help registering?
Contact support
Complete your profile and stay up to date
Contact Support
Create an ISMG account now
Create an ISMG account now
Need help registering?
Contact support
Sign in now
Need help registering?
Contact support
Sign in now
Our website uses cookies. Cookies enable us to provide the best experience possible and help us understand how visitors use our website. By browsing bankinfosecurity.com, you agree to our use of cookies.
Author
Administraroot