Cybersecurity news, threat research, and more from the leader in making breach prevention easy
A non-fungible token (NFT) is a record on a blockchain associated with a digital or physical asset—usually a digital file such as a photo, video, or audio. An NFT’s ownership is recorded in the blockchain, and it can be sold and traded. NFTs differ from cryptocurrencies, which are mostly fungible, in that NFTs are unique and non-substitutable. The NFT market is booming, with trading volume exploding by over 20,000 percent from 2020 to 2021. Cybercriminals have rushed to exploit this trend, which the Morphisec Threat Labs team has previously examined in a white paper. The Threat Labs team now has fresh research on the crypto and NFT malware NFT-001, which first surfaced in November 2020.
The NFT-001 attack sequence typically includes the following steps:
The threat actor has now switched from the Babadeda crypter to a new staged downloader while using the same delivery infrastructure as before. The new downloader adds increased defense evasion abilities to this malware. 
Morphisec Labs has tracked several waves of the NFT malware delivering the Remcos RAT since it first surfaced. In June 2022 we found a shift in the crypter used to deliver the Remcos RAT. The Babadeda crypter has now been discarded for a new staged downloader.
The malware delivery hasn’t changed much. It sends a user a private message enticing them to download a related application supposedly granting the user access to the newest features. Below is an example of the phishing message targeting users of “Dune”—an Ethereum-based crypto data analytics platform.
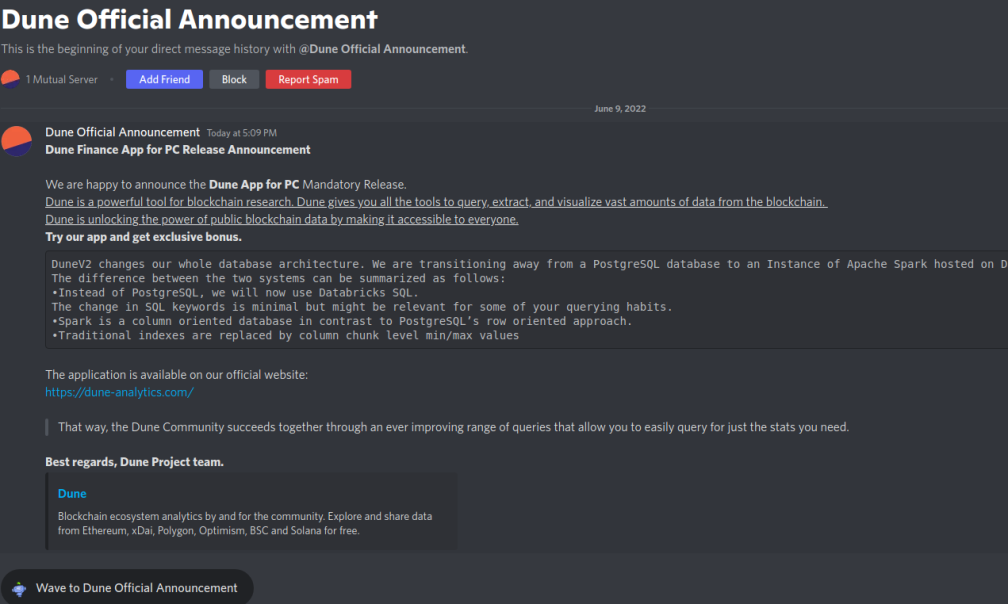 If a user clicks the hyperlink in the message, it directs him to a decoy website that mimics the original. There, the user is prompted to download the malicious “installer” which infects the victim’s machine with the Remcos RAT.
If a user clicks the hyperlink in the message, it directs him to a decoy website that mimics the original. There, the user is prompted to download the malicious “installer” which infects the victim’s machine with the Remcos RAT.
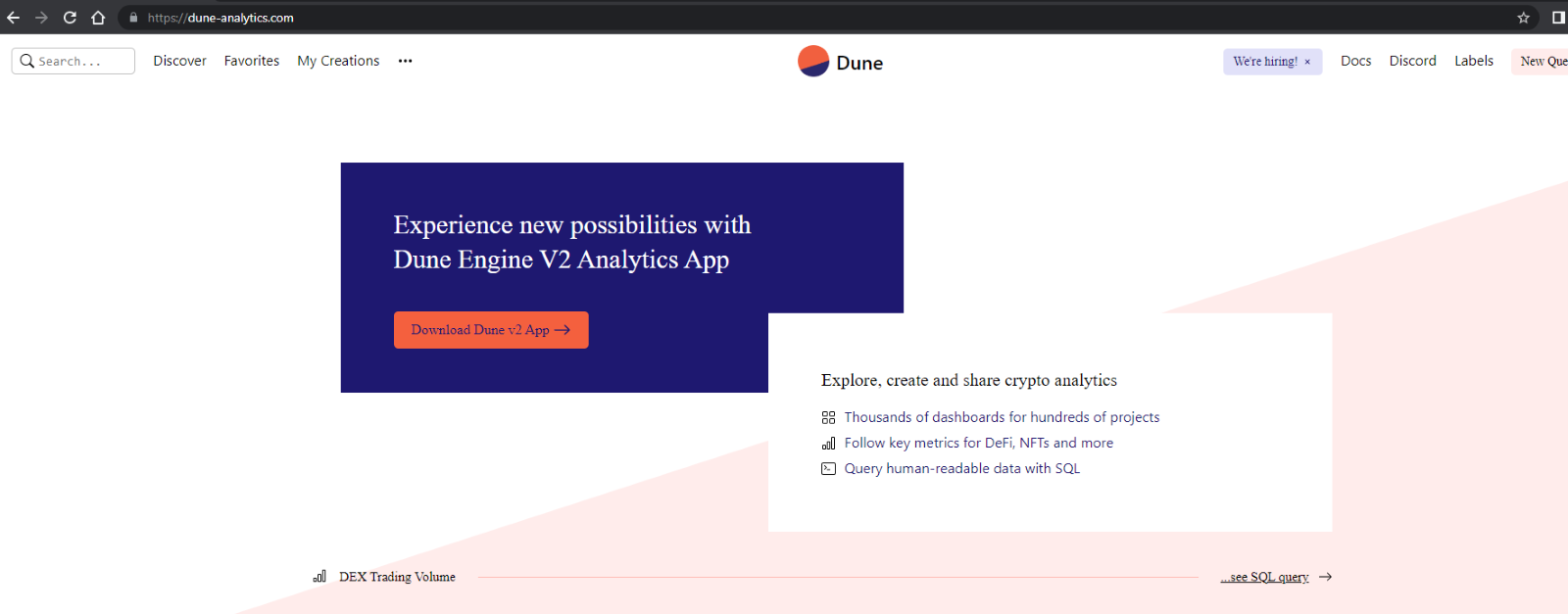
For more information on the infrastructure, read Morphisec’s previously mentioned white paper, “Journey of a Crypto Scammer.”
The threat actor keeps the first stage “installers” with a low detection rate.
 The execution starts by performing a User Account Control (UAC) bypass. It hijacks the default handler for the ms-settings protocol and sets it to execute a Powershell command that adds the C: folder to the Windows Defender exclusion list. The code that performs this UAC bypass technique is well documented in the open-source repository. But the attacker employed it extremely poorly—he didn’t even bother to remove unnecessary WinAPI calls, such as printing to the console.
The execution starts by performing a User Account Control (UAC) bypass. It hijacks the default handler for the ms-settings protocol and sets it to execute a Powershell command that adds the C: folder to the Windows Defender exclusion list. The code that performs this UAC bypass technique is well documented in the open-source repository. But the attacker employed it extremely poorly—he didn’t even bother to remove unnecessary WinAPI calls, such as printing to the console. 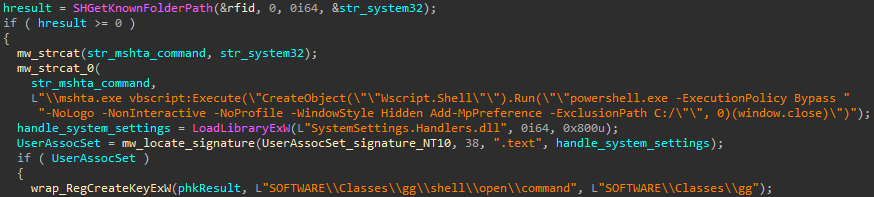 After excluding the C: folder from Windows Defender, the following Powershell commands are de-obfuscated and executed:
After excluding the C: folder from Windows Defender, the following Powershell commands are de-obfuscated and executed:
1) The first Powershell command downloads and executes a plain Remcos RAT (C2 – 144.91.79[.]86).
The C2 used in that Remcos RAT was also seen in the wild in samples using the Babadeda crypter. This bolsters our suspicion it’s the same threat actor.
We also noticed a variant of this downloader in the Tandem Espionage campaign shares commonalities with this campaign:
Though the URL downloading the Eternity stealer is the same, we think these may be two different threat actors that used the same downloader as a service.
The crypto and NFT communities are on the cutting edge of financial innovation, and they are a lucrative target for attackers. This naturally means there’s more scope for threat actors to exploit gaps in such rapidly evolving technology. This new staged downloader for NFT-001 is more evasive than the earlier version, increasing its ability to sneak past traditional cybersecurity solutions. According to the latest Picus report, defense evasion is now the most popular tactic among malware operators.
This tactic is popular because there aren’t many effective tools against defense evasion. One such tool is Morphisec’s revolutionary Moving Target Defense (MTD) technology, which comprehensively prevents defense evasion techniques. Unlike other cybersecurity solutions which focus on detecting known patterns with response playbooks, MTD preemptively blocks attacks on memory and applications and remediates the need for a response. To learn more about Morphisec’s revolutionary Moving Target Defense technology, read the white paper: Zero Trust + Moving Target Defense: The Ultimate Ransomware Strategy. 
Samples
Stay in the loop with industry insight, cyber security trends, and cyber attack information and company updates.
Author
Administraroot


